QRR Cybersecurity
Relation-Primary Authentication
🔒
The next generation of cybersecurity
Blocks attacks that traditional systems miss
The Credential Theft Crisis
81% of breaches involve stolen credentials
Traditional Security Fails When:
- Attacker has valid username + password
- Credentials stolen from data breach
- Phishing attack succeeds
- Session hijacking occurs
- Insider threat with legitimate access
Having the right password is no longer enough
Context matters
Real-Time Monitoring
Live security metrics you can see
How QRR Works
1. Relational Field Analysis
Calculates mathematical relationships between location, device, time, and behavioral patterns
2. Coherence Verification
Measures if all relationships "cohere" with established baseline patterns
3. Adaptive Learning
Automatically adjusts to legitimate user drift while blocking anomalous access
The key insight: Security isn't about checking attributes—it's about verifying relationships
Credential Stuffing Attack
Same credentials, different outcome
Traditional System: ALLOWED ✗
- ✅ Username: correct
- ✅ Password: correct
- → Access granted - No context checking
QRR System: BLOCKED ✓
- ✅ Username: correct
- ✅ Password: correct
- ❌ Location coherence: 0.23 (critical)
- ❌ Device fingerprint: no match
- ❌ Temporal pattern: anomalous
- → Access denied - Relational field incoherent
Live Dashboard in Action
Real-time monitoring catches attacks traditional systems miss
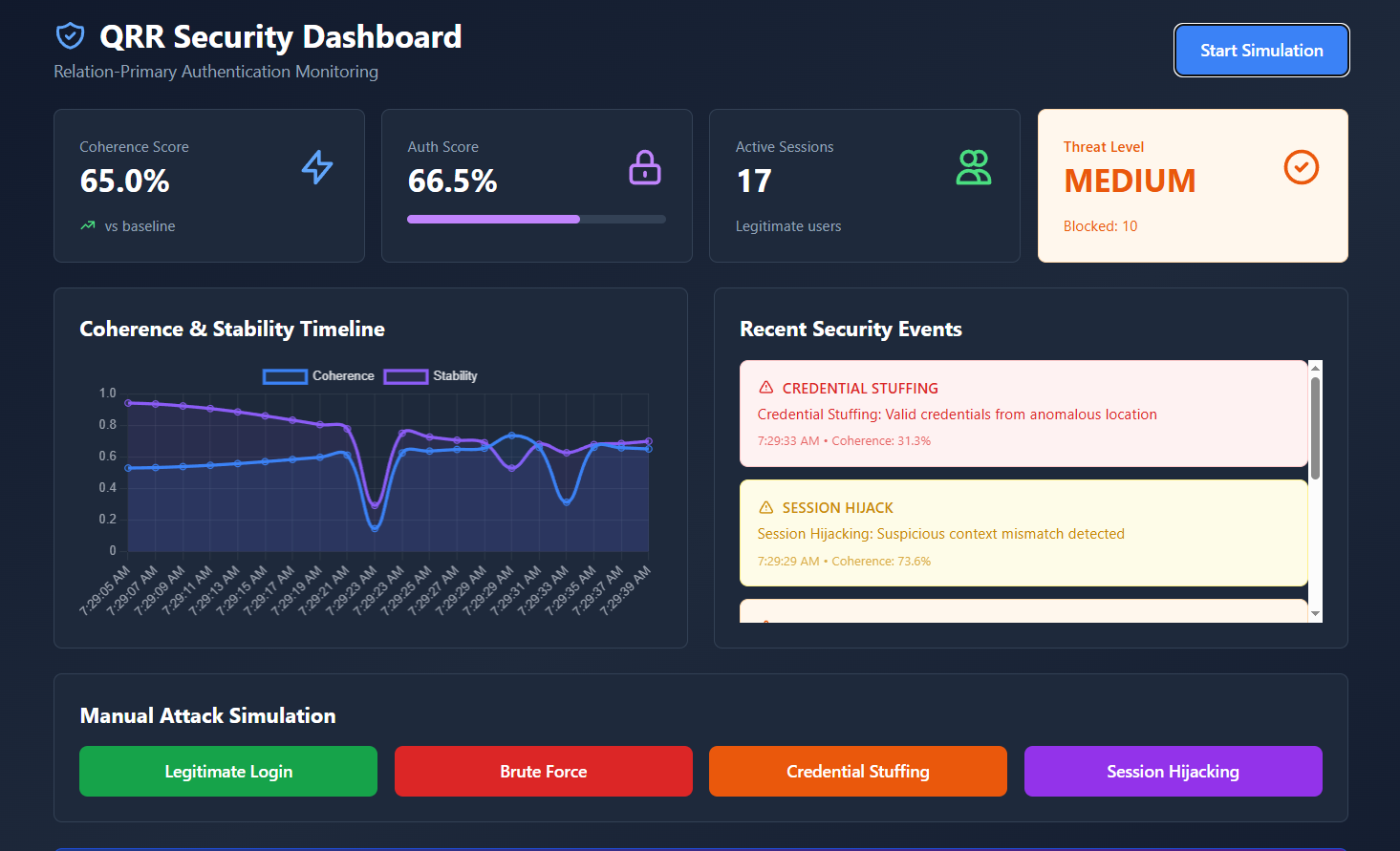
Actual QRR dashboard detecting credential stuffing and session hijacking attacks
Traditional vs QRR Security
Object-Primary
- Static attributes only
- No context awareness
- Vulnerable to credential theft
- Reactive detection
- High false negatives
Relation-Primary
- Relational field analysis
- Full context awareness
- Blocks stolen credentials
- Proactive detection
- Adapts to legitimate drift
QRR detects attacks that have the right password but wrong context
See It In Action
Experience relation-primary authentication
Interactive Demo Features:
- Real-time coherence monitoring
- Simulated attack scenarios
- Live threat detection
- Interactive metrics dashboard
Contact for Enterprise Deployment
Robin Macomber
relationalrelativity@gmail.com
805-621-0987